Introduction – The Evolution of IoT and the Software Management Challenge
Between 2015 and 2024, the Internet of Things experienced significant growth: from simple environmental sensors to complex industrial systems, the number of connected devices increased from 3.8 billion to 18.5 billion, marking a growth of 387%.
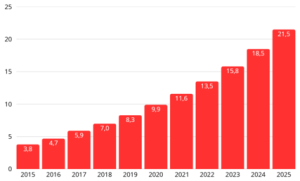
With this massive expansion, a crucial challenge has emerged: how to update the software running on millions of distributed field devices in a secure, reliable, and scalable way? OTA (Over-The-Air) updates have evolved from a convenience to an essential component for ensuring security, operational continuity, and functional improvements without physically accessing the hardware.
However, building a robust and scalable OTA infrastructure presents complex technical challenges. This is where Mender comes into play—an open-source platform designed to simplify and secure the software update process for Linux-based devices, turning technical complexity into a manageable solution.

What Is Mender and Why Use It
Mender is an enterprise-grade solution designed to provide OTA updates to Linux-based devices, with a particular focus on security, reliability, and ease of integration.
The platform stands out for its ability to handle complex deployments in industrial settings and in all contexts where ensuring service continuity and minimizing operational risk is crucial.
As an open-source solution, Mender offers:
- full transparency on how it works,
- high flexibility for customization,
- a solid base on which to build tailored OTA solutions.
Its modular design allows you to start with basic functionalities—such as full system image updates—and later extend to application updates, containers, software packages, or specific configurations, adapting to the evolving needs of the project.
OTA: From Technical Requirement to Legal Obligation
In a hyperconnected world, not updating devices means exposing them to vulnerabilities, service outages, and non-compliance.
Companies relying on manual strategies or custom scripts face:
- Long update times
- Unmanaged errors and rollbacks
- Fragile and untraceable infrastructures
- Fines related to non-compliance (up to €15 million or 2.5% of revenue, according to the CRA)
OTA (Over-The-Air) updates therefore become a functional, operational, and legal requirement. You need a solution that is:
- Scalable, to manage thousands of devices
- Secure, with signing, rollback, and authentication
- Standardized, to meet audits and regulations
Our Problem Analysis: Why OTA Updates Are Critical
Through years of projects in various industries such as industrial or energy, we have identified the main pain points companies face in IoT software management:
- Operational Risk: Unupdated devices expose companies to security vulnerabilities and malfunctions that can cause costly disruptions.
- Logistical Complexity: Manually updating thousands of distributed devices is impractical and generates prohibitive costs.
- Regulatory Compliance: With the introduction of the Cyber Resilience Act, automatic updates become a legal obligation, not just a technical choice.
- Lack of Control: Without a structured OTA strategy, companies lose visibility and control over their distributed digital assets.
AIknow solves these issues through a systematic approach that combines strategic consulting, technical implementation, and continuous operational support.
The AIknow Methodology: From Strategy to Implementation
Our experience has led us to develop a consolidated process that guides clients through every phase of their OTA project:
1. Assessment and Strategy
We analyze the existing architecture, business requirements, and regulatory constraints to define the most suitable OTA strategy. We evaluate factors such as:
- Type and distribution of devices
- Uptime requirements and operational criticality
- Regulatory compliance (CRA, industry-specific)
- Existing IT infrastructure and company policies
2. Technology Selection and Architecture Design
After evaluating multiple solutions on the market, we chose Mender as our reference technology platform for its maturity, security, and flexibility. Mender allows us to offer clients:
- Modular architecture with a device-side client and centralized server
- Support for atomic updates with automatic rollback
- Native integration with embedded Linux ecosystems (Yocto Project)
- Cloud or on-premise deployment options
3. Implementation and Integration
Our team manages the entire technical implementation:
- Preparation of OS images and integration with existing build pipelines
- Configuration and hardening of the Mender server
- Setup of testing and validation procedures
- Integration with company monitoring and alerting systems
4. Training and Handover
We train the client’s internal teams to ensure operational autonomy, providing tailored documentation and best practices specific to their context.
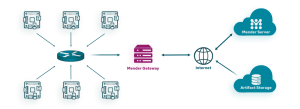
How we implement Mender: our hands-on approach
Our implementation methodology is based on years of experience and lessons learned from real-world projects:
Development environment preparation: We configure integration with Yocto Project using the meta-mender layers, optimizing partition configuration to support secure dual-rootfs updates and automatic rollbacks.
Customized infrastructure setup: We implement the Mender server according to the customer’s specific needs—cloud for startups and SMEs focused on time-to-market, on-premise for enterprises with strict security requirements or data sovereignty policies.
Optimized DevOps pipeline: We integrate Mender into the client’s existing CI/CD pipelines, automating artifact generation, validation tests, and controlled deployment. This approach drastically reduces manual errors and accelerates release cycles.
Progressive rollout management: We implement canary deployment and phased rollout strategies, allowing updates to be tested on a limited group of devices before full distribution, minimizing operational risk.
The result is a robust, secure OTA infrastructure perfectly integrated into the client’s technological ecosystem.
Security by design: our protection-first approach
Security is at the core of our implementation methodology. Every OTA solution we design incorporates:
- End-to-end encryption: All updates are digitally signed and client-server communication is protected via TLS with enterprise-grade certificate management best practices.
- Automatic rollback mechanisms: In the event of a failed update, devices automatically revert to the previous working version, avoiding costly downtime and manual intervention.
- Complete audit trail: Every operation is tracked and logged, providing full visibility for compliance and troubleshooting.
- Granular access control: We implement role-based authorization systems to ensure only authorized users can manage critical updates.

Management interface and automation: the AIknow user experience
We customize the Mender management interface based on the customer’s operational needs:
- Custom dashboards: We configure the web UI to display the most relevant metrics for the client’s business, integrating alerts and notifications with existing monitoring systems.
- API integration: We leverage Mender’s REST APIs to integrate OTA management into the client’s enterprise systems (ERP, ITSM, monitoring platforms), creating a coherent and automated ecosystem.
- Standardized operational procedures: We define workflows and operational procedures that ensure consistency and reduce the risk of human error in critical operations.
AIknow and the Cyber Resilience Act: turning compliance into a competitive advantage
The Cyber Resilience Act (CRA), effective from December 2024 and fully enforceable by December 2027, represents a significant challenge for many IoT companies. AIknow has developed specific expertise to turn this regulatory requirement into a strategic opportunity.
Our approach to CRA compliance
- Regulatory readiness assessment: We analyze the customer’s product portfolio to identify compliance gaps and define a prioritized remediation roadmap.
- Implementation of technical requirements: Our solution based on Mender natively meets CRA requirements:
- Automatic and timely updates (Annex 1.2c)
- Full software lifecycle management
- Automatic generation and maintenance of a Software Bill of Materials (SBOM)
- Audit trail to demonstrate compliance
AIknow’s distinctive value in compliance
- Cross-industry experience: Our knowledge across different sectors allows us to apply proven best practices and anticipate specific requirements.
- Risk reduction: CRA penalties can reach €15 million or 2.5% of global turnover. Our structured approach significantly minimizes these risks.
- Accelerated time-to-compliance: Thanks to our proven methodology, we reduce implementation times compared to internal developments or ad-hoc approaches.
- Future readiness: Our architecture is designed to evolve with future regulatory changes and the expansion toward AI and edge computing.
Conclusion – AIknow, your strategic partner for OTA transformation
The evolution of IoT and the introduction of the Cyber Resilience Act require a structured approach and specialized expertise that go beyond simple technological implementation. AIknow positions itself as a strategic partner that guides companies through this transformation, turning technical complexities and regulatory constraints into sustainable competitive advantages.
Our consolidated methodology, based on years of experience and the use of mature technologies such as Mender, enables the implementation of robust, secure, and compliance-ready OTA solutions in a short time and with controlled risks. However, our approach remains technology-agnostic: while we consider Mender one of the most solid solutions on the market, we always evaluate the client’s specific needs and, when necessary, can integrate or recommend alternative technologies best suited to the company context and project requirements.
With the 2027 CRA deadline approaching, choosing the right partner becomes critical for the success of IoT projects. AIknow offers not only technical expertise but also a strategic vision that aligns technology, business, and regulatory compliance, always with the flexibility needed to adapt to your unique needs.
Do you want to turn your IoT device management into a competitive advantage? Our team of experts is ready to evaluate your specific situation and design a tailored strategy for you.


